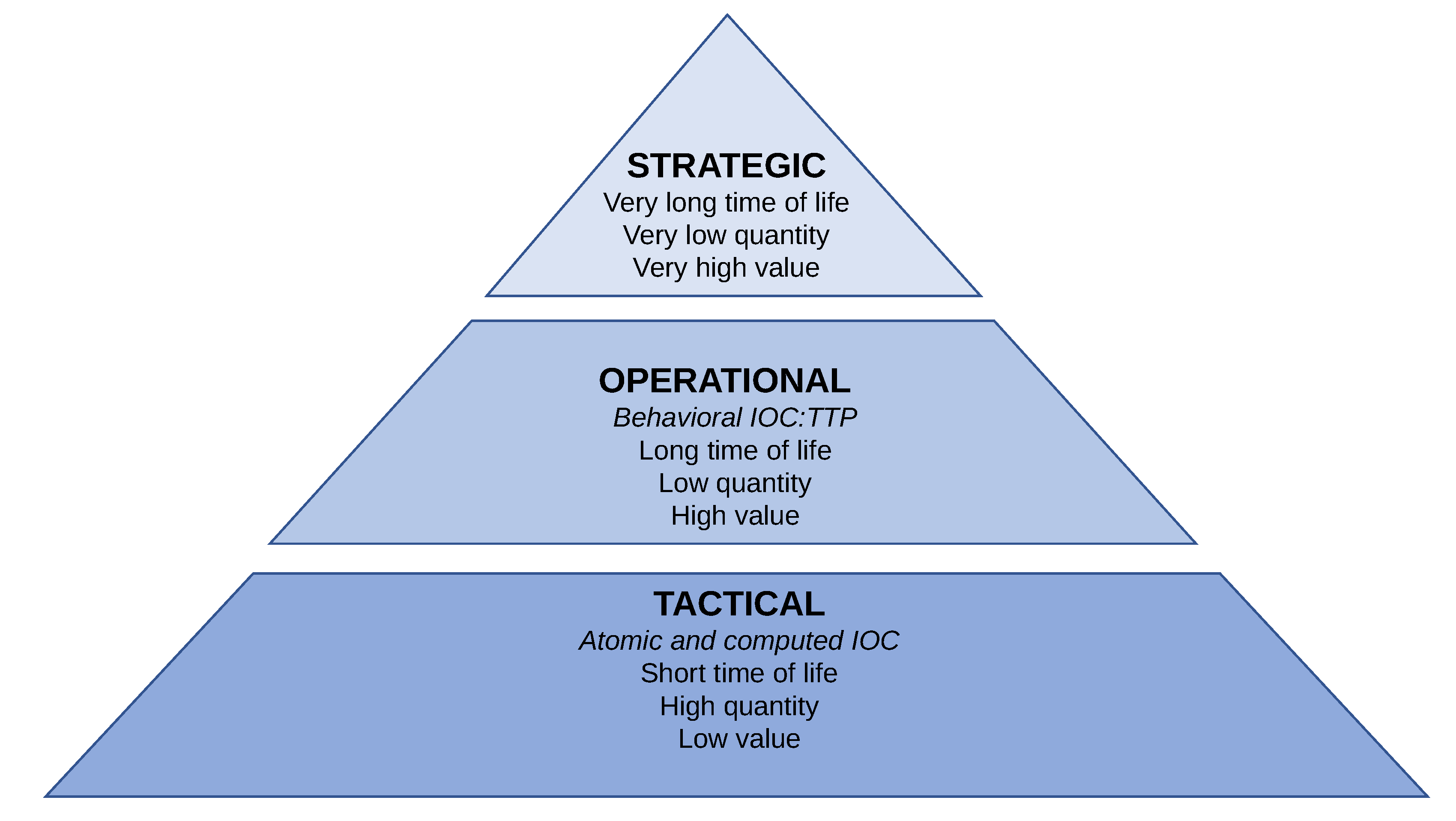
Key Indicators Of Compromise . indicators of compromise (iocs) are artifacts that indicate a potential intrusion. analyzing indicators of compromise involves monitoring for potential signs of a security breach or compromise. indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. This guide explores the types of iocs, their. Iocs are data that indicate a system may have been infiltrated. indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. For example, iocs can be. learn what iocs are, how they work, and the most common types. an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an.
from www.mdpi.com
Iocs are data that indicate a system may have been infiltrated. analyzing indicators of compromise involves monitoring for potential signs of a security breach or compromise. an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. indicators of compromise (iocs) are artifacts that indicate a potential intrusion. learn what iocs are, how they work, and the most common types. This guide explores the types of iocs, their. indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an. indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. For example, iocs can be.
Electronics Free FullText Key Requirements for the Detection and
Key Indicators Of Compromise Iocs are data that indicate a system may have been infiltrated. indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an. indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. For example, iocs can be. analyzing indicators of compromise involves monitoring for potential signs of a security breach or compromise. indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Iocs are data that indicate a system may have been infiltrated. an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. learn what iocs are, how they work, and the most common types. This guide explores the types of iocs, their. indicators of compromise (iocs) are artifacts that indicate a potential intrusion.
From www.makeuseof.com
What Do the Indicators of Compromise Mean? The Best Tools to Help Key Indicators Of Compromise indicators of compromise (iocs) are artifacts that indicate a potential intrusion. indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. indicators of compromise (iocs) are. Key Indicators Of Compromise.
From www.lepide.com
What are Indicators of Compromise? Key Indicators Of Compromise indicators of compromise (iocs) are artifacts that indicate a potential intrusion. indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. learn what iocs are, how they work, and the most common types. This guide explores the types of iocs, their. an indicator of. Key Indicators Of Compromise.
From www.trendmicro.com.my
Empowering the Analyst Indicators of Compromise Security News Key Indicators Of Compromise indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. learn what iocs are, how they work, and the most common types. an indicator of compromise. Key Indicators Of Compromise.
From www.salvagedata.com
Cyber Security Awareness What Are Indicators of Compromise (IoC Key Indicators Of Compromise analyzing indicators of compromise involves monitoring for potential signs of a security breach or compromise. indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an. indicators of compromise (iocs) are artifacts that indicate a potential intrusion. Iocs are data that indicate a system may have been infiltrated. . Key Indicators Of Compromise.
From www.alamy.com
Handwriting text writing Identify Indicators Of Compromise. Concept Key Indicators Of Compromise indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an. Iocs are data that indicate a system may have been infiltrated. learn what iocs are, how. Key Indicators Of Compromise.
From darwinsdata.com
What is an example of an indicator of compromise? Darwin's Data Key Indicators Of Compromise an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. indicators of compromise (iocs) are artifacts that indicate a potential intrusion. This guide explores the types of iocs, their. learn what iocs are, how they work, and the most common types. For example, iocs can be. indicators of compromise. Key Indicators Of Compromise.
From www.sekoia.io
What is an Indicator of Compromise (IoC)? SEKOIA.IO Key Indicators Of Compromise This guide explores the types of iocs, their. Iocs are data that indicate a system may have been infiltrated. indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. indicators of compromise (iocs) are information about a specific security breach that can help security teams determine. Key Indicators Of Compromise.
From www.teramind.co
10 Indicators of Compromise (IOC) Examples To Look Out For Key Indicators Of Compromise learn what iocs are, how they work, and the most common types. indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an. indicators of compromise (iocs) are artifacts that indicate a potential intrusion. indicators of compromise are behaviors or data which show that a data breach, intrusion,. Key Indicators Of Compromise.
From www.crowdstrike.com
IOC Security Indicators of Attack vs. Indicators of Compromise Key Indicators Of Compromise indicators of compromise (ioc) in cybersecurity refers to clues or evidence that suggest a network or system has been breached or attacked. Iocs are data that indicate a system may have been infiltrated. For example, iocs can be. This guide explores the types of iocs, their. indicators of compromise (iocs) are artifacts that indicate a potential intrusion. . Key Indicators Of Compromise.
From www.dreamstime.com
Handwriting Text Writing Indicators of Compromise. Concept Meaning Key Indicators Of Compromise This guide explores the types of iocs, their. For example, iocs can be. learn what iocs are, how they work, and the most common types. indicators of compromise (iocs) are artifacts that indicate a potential intrusion. an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. Iocs are data that. Key Indicators Of Compromise.
From www.trendmicro.com.ph
Indicators of compromise Definition Key Indicators Of Compromise learn what iocs are, how they work, and the most common types. indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an. For example, iocs can be. analyzing indicators of compromise involves monitoring for potential signs of a security breach or compromise. an indicator of compromise (ioc). Key Indicators Of Compromise.
From www.dreamstime.com
Writing Note Showing Indicators of Compromise. Business Photo Key Indicators Of Compromise indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. For example, iocs can be. analyzing indicators of compromise involves monitoring for potential signs of a security breach or compromise. indicators. Key Indicators Of Compromise.
From www.mdpi.com
Electronics Free FullText Key Requirements for the Detection and Key Indicators Of Compromise learn what iocs are, how they work, and the most common types. indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. indicators of compromise (iocs) are information about a specific. Key Indicators Of Compromise.
From www.xcitium.com
What are Indicators of Compromise Security? IOC Meaning Key Indicators Of Compromise indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. Iocs are data that indicate a system may have been infiltrated. indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an. indicators of compromise (ioc) in cybersecurity refers to clues. Key Indicators Of Compromise.
From www.armordot.com
Indicators of Compromise in Threat Intelligence Let's speak some Key Indicators Of Compromise analyzing indicators of compromise involves monitoring for potential signs of a security breach or compromise. For example, iocs can be. an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. indicators of compromise (iocs) are artifacts that indicate a potential intrusion. learn what iocs are, how they work, and. Key Indicators Of Compromise.
From virtualarmour.com
Identifying a Breach Finding Indicators of Compromise (IOC) Key Indicators Of Compromise an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. This guide explores the types of iocs, their. For example, iocs can be. indicators of compromise (iocs) are information about a specific security breach that can help security teams determine if an. indicators of compromise (iocs) are artifacts that indicate. Key Indicators Of Compromise.
From www.dreamstime.com
Writing Note Showing Indicators of Compromise. Business Photo Key Indicators Of Compromise indicators of compromise (iocs) are artifacts that indicate a potential intrusion. indicators of compromise are behaviors or data which show that a data breach, intrusion, or cyberattack has occurred. learn what iocs are, how they work, and the most common types. indicators of compromise (iocs) are information about a specific security breach that can help security. Key Indicators Of Compromise.
From www.dreamstime.com
Conceptual Hand Writing Showing Indicators of Compromise. Business Key Indicators Of Compromise analyzing indicators of compromise involves monitoring for potential signs of a security breach or compromise. an indicator of compromise (ioc) is evidence that someone may have breached an organization’s network or endpoint. learn what iocs are, how they work, and the most common types. indicators of compromise are behaviors or data which show that a data. Key Indicators Of Compromise.